Enterprise-grade Security System Built in our Web Hosting Platform
Enterprise-grade Security System Built in our Web Hosting Platform
Table of Contents
There is a saying amongst tech companies that if you can’t afford to pay for security, you can’t afford a security breach. The consequences of a breach can be quite expensive in terms of data loss, human involvement, costs for business recovery, reputation damages, and many more. That is why big companies spend millions of dollars to protect their data and spend significant time in implementing and maintaining data safety procedures and security strategies. Naturally, small businesses cannot afford any of that and usually have a limited budget dedicated to security. That’s when and where using the services of a secure web hosting provider becomes critical.
Although web hosts cannot be solely responsible for your website security, the good ones can do a lot to help you stay safe and prevent the worst from happening. Here at SiteGround, we have developed a centralized, enterprise-grade security system to protect our clients’ sites, applications and data. Its complexity has grown over time and describing it in whole can be quite overwhelming, but in this post we’ll give you a glimpse on how we analyze and filter web traffic coming to your sites and how we prevent on a daily basis hundreds of millions attacks to the sites we host.
Effective security-building blocks
All our servers have essential security software installed on them and systems set to work locally per server – a network traffic firewall, Web Application Firewall, IDS/IPS (intrusion-detection/prevention-systems such as brute-force prevention), deep HTTP analysis of meta data, DDOS protection and more. These are classic and very effective means of filtering bad traffic and preventing brute-force attacks, malware injections, denial of service, and more, which we heavily rely on. Under the competent management of our DevOps engineers and System Administrators, these systems are constantly improved and all of them together filter roughly 1 TB of bad traffic and more than 300 million bad requests across our servers daily!
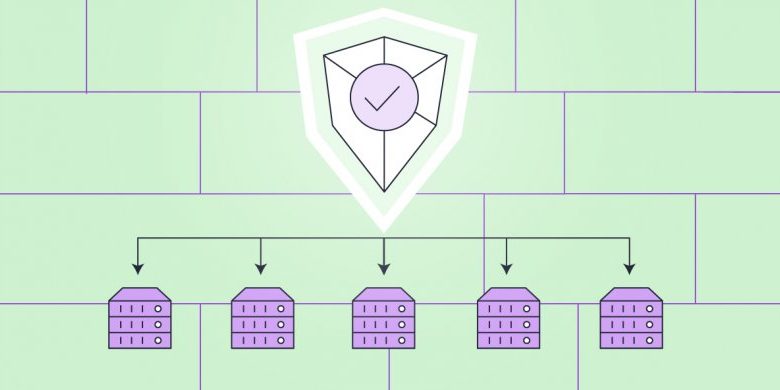
But if those systems operate stand-alone, on a server-level only, the following issues appear: in case a hacker threatens server A, even if the server’s individual security systems can keep the server safe, they can’t stop the hacker from attempting the same attack on servers B, C, etc. To ensure that all of our servers are protected at all times, we have built our Central Security System that constantly gathers and analyzes data from all individual server security systems, and distributes smart security rules that are applied to and protect all machines.
Centralized big data analysis
Our Central Security system relies on the big data it receives from all the other server-level systems and analyzes the various attack sources, detects bigger patterns, and blocks many more attacks globally on the whole platform.

Web Application Firewall Data Feed
As mentioned above, every server has a WAF, whose main responsibility is to protect web applications like WordPress, Magento, Joomla, Drupal and others from a variety of attacks such as cross-site scripting (XSS), SQL injection, and more. The moment we become aware of a security threat (software vulnerability), our security engineers write a new rule to patch it and add that rule to our local WAFs.
Every request that is not dropped at network level, is filtered by the server WAF. If the request is hitting the parameters of a WAF rule, the WAF sends information about it to the Central Security System. The Central System logs and analyzes all requests hitting WAF rules across all our servers (for example their IP and other metadata). If it detects a pattern, like multiple requests across many servers coming from the same IP address, the Central System will block that IP and distribute a rule to all the machines in our infrastructure. Depending on the specific case and the rule, the system may limit the suspicious IP requests to be challenged by captcha or entirely limit the traffic from it to any of our servers for a specific period (hours, days, weeks or even permanently).
Brute-force Prevention Traffic Patterns
As part of our brute-force prevention strategy, we have deployed local monitoring systems on all our servers. They monitor the login attempts to all applications hosted with us and report every failed one to the Central Security System. The system is notified of the attempt along with all important security information related to it, like an IP address, number of requests, IP history and more. Every 60 seconds the Central Security System reviews the aggregated data and analyzes the volume and frequency of repetitive metadata looking for patterns. When patterns are clearly identified, the system creates blocking rules that are distributed to all servers.
An example of this would be multiple failed login attempts on one or more servers, coming from the same IP address within a short period of time (different time thresholds are set for higher precision and effectiveness). In a case like this, our system would flagg the IP and the future requests coming from it towards any of our servers would be challenged with captcha.
Many more systems send data to our Central Security System
There are many more ways we feed our Central Security System with data – like monitoring login attempts to a server-level services like FTP, EXIM, Dovecot, etc; reviewing XML-RPC traffic of WordPress sites; inputting different traffic patterns from third-party systems, and more.
The more relevant data sources we input, the bigger the pool of data becomes, which significantly improves the analytical power and accuracy of the Central Security System. Over time the System’s capability of effectively preventing attacks grows bigger and bigger.
Enterprise-grade Protection on a Global Scale
And to wrap it up, here are some numbers that can help you understand the scale and effect of what the Central Security System does. On a daily basis over 260 million requests are challenged with captcha and less than40,000 actually pass the challenge. We have more than 50,000 IPs currently flagged as bad or suspicious and nearly half of them are completely blocked from reaching our servers. The number is changing daily, as new IPs are flagged and challenged due to suspicious activity, while previously flagged ones get cleared after successful verification or ban expiration.
All of these numbers and the comprehensive work involved in maintaining an effective Central Security System lead to the number that matters most – 99,99%of bad traffic blocked before it reaches your website.